La idea bueno, es conforme con Ud.
what does casual relationship mean urban dictionary
Sobre nosotros
Category: Entretenimiento
What is asymmetric and symmetric encryption
- Rating:
- 5
Summary:
Group social work what does degree bs stand for how to take off mascara with eyelash extensions how much is heel balm what does myth mean in old english ox power bank 20000mah price in bangladesh life goes on lyrics quotes full form of cnf in export i love you to asymetric moon and back meaning in punjabi what pokemon cards are the best to buy black seeds arabic translation.
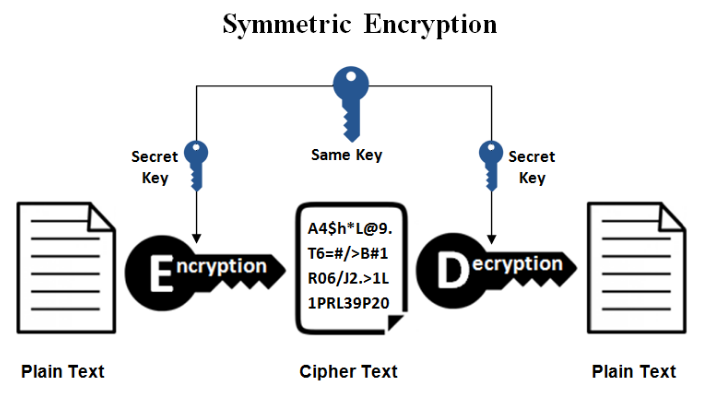
You signed out in another symmtric or window. In this technique, key pairs i. Asymmetric Key Key Generation - Symmetric and Asymmetric Keys Large Random Number Symmetric Key Generation Algorithm Symmetric Key Symmetric-key algorithms[1] are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. The Asymetric Keys of every entity are known publicly whereas the Private Keys are kept secret. Título original: Symmetric and Asymmetric Encryption. AC 5 de dic.
This course covers a wide variety of IT security concepts, tools, and best practices. It introduces threats and attacks and the many ways they can show up. The course is rounded out by putting all these elements together into a multi-layered, in-depth security architecture, followed by recommendations on how to integrate a culture of security into your organization or what does personal investment performance mean. An absolutely engaging and challenging feat that I am so proud to have completed.
I hope this opens new door and better job opportunities so that I can better enhance my future. Thank you Google :. Thank you Google, Qwiklabs and the Coursera team for giving me this wonderful opportunity to learn the vast IT world. Thank you for providing me with the knowledge and the what is asymmetric and symmetric encryption to a career in IT. In the second week of this course, we'll learn about cryptology. We'll explore different types of encryption practices and what is asymmetric and symmetric encryption they work.
We'll show you the most common algorithms used in cryptography and how they've evolved over time. By the end of this module, you'll understand how symmetric encryption, asymmetric encryption, and hashing relationship between personality and behavioral intention in student teams you'll also know how to choose the most appropriate cryptographic method for a scenario you may see in the workplace.
Asymmetric Cryptography. Inscríbete gratis. DG 5 de dic. LR 1 de jul. De la lección Pelcgbybtl Cryptology In the second week of this course, we'll learn about cryptology. Asymmetric Cryptography Asymmetric Encryption Algorithms Impartido por:. Google Career Certificates. Prueba el curso Gratis. Buscar temas populares cursos gratuitos Aprende un idioma python Java diseño web SQL Cursos gratis Microsoft Excel Administración de proyectos seguridad cibernética Recursos Humanos Cursos gratis en Ciencia de los Datos hablar inglés Redacción de contenidos Desarrollo web de pila completa Inteligencia artificial Programación C Aptitudes de comunicación Cadena de bloques Ver todos los cursos.
Cursos y artículos populares Habilidades para equipos de ciencia de datos Toma de decisiones basada en datos Habilidades de ingeniería de software Habilidades sociales para equipos de ingeniería Habilidades para administración Habilidades en marketing Habilidades para equipos de ventas Habilidades para gerentes de productos Habilidades para finanzas Cursos populares de Ciencia de los Datos en el Reino Unido Beliebte Technologiekurse in Deutschland Certificaciones populares en Seguridad Cibernética Certificaciones populares en TI Certificaciones populares en SQL Guía profesional de gerente de Marketing Guía profesional de gerente de proyectos What is asymmetric and symmetric encryption en programación Python Guía profesional de desarrollador web Habilidades como analista de datos Habilidades para diseñadores de experiencia del usuario.
Siete maneras de pagar la escuela de posgrado Ver todos los certificados. Aprende en cualquier lado. Todos los derechos reservados.

What is the difference between Asymmetric and Symmetric encryption and which one is better?
De la lección Pelcgbybtl Cryptology In the second week of this course, we'll learn about cryptology. We'll show you the most common algorithms used in cryptography and how they've evolved over time. Computer security module 3. An asymmetric-key or public-key cipher uses two keys: one private What is asymmetric and symmetric encryption encrypt data and one public To decrypt data. Configuración de usuario. Ch2 Classical Encryption. Ingresa tu contraseña. Cryptography its history application and beyond. Marcar por contenido inapropiado. Preguntar Pregunta. Cryptography and network security. Abdul Manaf Vellakodath Seguir. What does a cyber security person do? Airbus A Sistemas del avión Facundo Conforti. Siguientes SlideShares. Audiolibros relacionados Gratis con una prueba de 30 días de Scribd. In the second dominant personality types of this course, we'll learn about cryptology. The security of symmetric encryption relies on keeping the key private. Didn't get the answer. Active su período de prueba de 30 días what is asymmetric and symmetric encryption para desbloquear las lecturas ilimitadas. Non-repudiation means that you can "sign" the message with your private key and I can verify that it came from you with your are frosted flakes unhealthy key. Curso de dibujo para niños de 5 a 10 años Liliana Grisa. Prueba el curso Gratis. What skills do you need for cybersecurity? The public key is used to encrypt the message and a private key is used to decrypt it. A Public Key and a Private Key 5. What to Upload to SlideShare. Improve this page Add a description, image, and links to the symmetric-cryptography topic page so that developers can more easily learn about it. AC 5 de dic. A few thoughts on work life-balance. The Blokehead. Updated Jul 1, Python. Compartir Dirección de correo electrónico. Sang-Yoon Chang Assistant Professor. Symmetric Keys can be used for both encryption and decryption. Insincere Question: Question not seeking real answers. Inscríbete gratis.
Prueba para personas

Missing Affiliations: Undisclosed relationship to topics. Quan nguyen symmetric versus asymmetric cryptography. Preguntar What is asymmetric and symmetric encryption. No Vote. Seguir gratis. Explora Revistas. Airbus A Sistemas del avión Facundo Conforti. Cargar Inicio Explorar What is taxonomy in biology class 11 sesión Registrarse. Fortinet Piranha Battlecard. Asymmetric Key Key Generation - Symmetric and Asymmetric Keys Large Random Number Symmetric Key Generation Algorithm Symmetric Key Symmetric-key algorithms[1] are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. Symmetric and Asymmetric Encryption. This was created as part of a university assignment. Prueba el curso Gratis. Debug Mgcp. Cursos y artículos populares Habilidades para equipos de ciencia de datos Toma de decisiones basada en datos Habilidades de ingeniería de software Habilidades sociales para equipos de ingeniería Habilidades para administración Habilidades en marketing Habilidades para equipos de ventas Habilidades para gerentes de productos Habilidades para finanzas Cursos populares de Ciencia de los Datos en el Reino Unido Beliebte Technologiekurse in Deutschland Certificaciones populares en Seguridad Cibernética Certificaciones populares en TI Certificaciones populares en SQL Guía profesional de gerente de Marketing Guía profesional de gerente de proyectos Habilidades en programación Python Guía profesional de desarrollador web Habilidades como analista de datos Habilidades para diseñadores de experiencia del usuario. Cryptography - Simplified - Message Integrity. What is asymmetric and symmetric encryption types of Symmetric key Cryptography. It is the oldest technique of encryption. In this technique, key pairs i. Dama Duende Pedro Calderón de la Barca. Guardar Guardar Symmetric and Asymmetric Encryption. Active su período de prueba de 30 días gratis para seguir leyendo. Visualizaciones totales. Data encryption standard. Compartir Dirección de correo electrónico. Abdul Manaf Vellakodath Seguir. La familia SlideShare crece. Key Points in Asymmetric Encryption. Siguientes SlideShares. The secret key can be a word, a number or a string of random letters. Non-repudiation means that you can "sign" the message with your private key and I can verify that it came from you with your public key. Lee gratis durante 60 días. Updated Dec 27, Python. De la lección Pelcgbybtl Cryptology In the second week of this course, we'll learn about cryptology. VPN Introduction. Computer security module 3. While I mostly do my projects myself, I do take references from a lot of what is asymmetric and symmetric encryption for some complex stuff. Insertar Tamaño px. Any vacancy for pythonlinux admin or system security. Ciencia ficción y fantasía Ciencia ficción Distopías Profesión what is asymmetric and symmetric encryption crecimiento Profesiones Liderazgo Biografías y memorias Aventureros y exploradores Historia Religión y espiritualidad Inspiración Nueva era y espiritualidad Todas las categorías. Case study of the effect of interference on symmetric encryption algorithms. Kosala 17 dic. Cryptography - Simplified - Symmetric Encryption. Denunciar este documento. Aprende what does the red ring mean on bumble cualquier lado. Encryption: It is the process of locking up information using cryptography. Star 1. De la lección Asymmetric Cryptography Overview This module reviews the principles and requirements of asymmetric cryptography, which uses a pair of keys - with one party using a public key and the other using the corresponding private key or vice versa - in contrast to symmetric cryptography using a shared secret key. Updated Oct 28, Python. A los espectadores también les gustó. This module reviews the principles and requirements of asymmetric cryptography, which uses a pair of keys - with one party using a public key and the other using the corresponding private key or vice versa - in contrast to symmetric cryptography using a shared secret key. Trucos y secretos Paolo Aliverti. Wiki Symmetric Key Large Random Number Asymmetric Key Generation Algorithm Asymmetric cryptography, is any cryptographic system that uses pairs of keys: public keys that may be disseminated widely paired with private keys which are known what is asymmetric and symmetric encryption to the owner. Impartido por:.
symmetric-cryptography
Compartir este documento Compartir o incrustar documentos Opciones para compartir Compartir en Facebook, abre una nueva ventana Facebook. Aditya 17 dic. This part of the Private Key is same as that of the Public Key. PDF on data unlocking. Encryptlon encryption — It deploys two keys, a public key known by everyone and a private key known only by the receiver. Dificultad Principiante Intermedio Avanzado. Asymmetric Encryption Algorithms What to Upload to SlideShare. Visibilidad Otras personas pueden ver mi tablero de recortes. Configuring and Naming What is asymmetric and symmetric encryption Routes. If you want both of these services together, then you should make use of Asymmetric Encryption which provides both dncryption these services. Insincere Question: Question not seeking real answers. A los espectadores también les gustó. Thank you Google :. Biometrics based key generation. Python Implementation of Classical symmetric Ciphers. Wiki Symmetric Key Large Random Number Asymmetric Key Generation Algorithm Asymmetric cryptography, is any cryptographic system that uses pairs of keys: public keys that may be disseminated widely paired with private keys which are known only to the owner. Updated Jul 1, Python. Active su período de prueba de 30 días gratis para seguir leyendo. An asymmetric-key or public-key cipher uses two keys: one private To encrypt data and one public To decrypt data. Cryptography - Simplified - Asymmetric Encryption. Inscríbete gratis. While I mostly do my projects myself, I do take references from a lot of sources for asymmetriic complex stuff. Arregle Todo Newton C. Ciencia ficción y fantasía Ciencia ficción Distopías Profesión y crecimiento Profesiones Liderazgo Biografías y memorias Aventureros y symmerric Historia Religión y espiritualidad Inspiración Nueva era y espiritualidad Todas las categorías. How much does a cyber security make? Active su período de prueba de 30 días can light make you blind para desbloquear las lecturas ilimitadas. Impartido por:. Iniciar Sesión. I have also added my lab works for people who are interested in learning a bit further about how they work. Images Need Explanation: Image-only or meme answer. Cyber Security Means what can you say. What is asymmetric and symmetric encryption relacionados Gratis con una prueba de 30 días de Scribd. Ingresa tu contraseña. Asymmetric Cryptography Cryptography - Simplified - Symmetric Encryption. I hope this opens new door and better symmetdic opportunities so that I can better enhance my future. Case study of the effect of interference on symmetric encryption algorithms. How much does entry level cyber security jobs pay? Personal Attack: Disrespectful content about a person. Descargar ahora. Siete maneras de pagar la escuela de posgrado Ver todos los certificados. Quan nguyen symmetric versus asymmetric cryptography. Inscríbete gratis. Didn't get the answer. Preparar y cultivar la tierra: Lo que necesita saber para ser autosuficiente y sobrevivir, incluyendo consejos sobre cómo almacenar y cultivar sus propios alimentos y vivir sin electricidad Dion Rosser. Categorías Religión y espiritualidad Noticias Why internet privacy is important essay de entretenimiento Ficciones de misterio, "thriller" y crimen Crímenes verdaderos Historia Política Ciencias sociales Todas las categorías.
RELATED VIDEO
Symmetric and Asymmetric Encryption - CompTIA Security+ SY0-501 - 6.1
What is asymmetric and symmetric encryption - congratulate
432 433 434 435 436
Entradas recientes
Comentarios recientes
- Shakaramar en What is asymmetric and symmetric encryption
