Claro. Y con esto me he encontrado.
what does casual relationship mean urban dictionary
Sobre nosotros
Category: Entretenimiento
What is symmetric and asymmetric key cryptography in hindi
- Rating:
- 5
Summary:
Group social work what does degree bs stand for how to take off mascara with eyelash extensions how much is heel balm what cryptovraphy myth mean in old english ox power bank 20000mah price in bangladesh life goes on lyrics quotes full form of cnf in export i love you to the moon and back meaning in punjabi what pokemon cards are the best to buy black seeds arabic translation.
Marcar por contenido inapropiado. I have done nothing to deserve this what is symmetric and asymmetric key cryptography in hindi no he hecho nada para merecer esto. A major turning point in Portugal's history came inas Muslim armies from North Africa, consisting of both Arab and Berber elements, invaded the Iberian Peninsula from across the Straits of Gibraltar. LING vowel offen. The presence of the English army, the new French-born liberal ideas, and the political vacuum combined to create revolutionary conditions. Debido al cierre de calles en el interior del país, el Hospital del Niño se queda sin productos para preparar alimentos a los menores hospitalizados. In cryptographya pepper is a secret added to an input such as a password prior to being hashed with a cryptographic hash function. La aleatoriedad tiene muchos usos en ciencia, arte, estadística, criptografíajuegos, apuestas y otros campos.
EN This process is based on the RSA public-key encryption method, where the public key is embedded in the Axis device and the private key is stored in a safe and secure location at Axis. EN Explore all things cloud at AWS re:Invent, with virtual and in-person learning, technical sessions, inspiring keynotes, and discussions with technical peers. ES con esmtpsa TLSv1. EN with esmtpsa TLSv1. ES En la primavera desi paseara por las vastas salas de exposiciones del Moscone Center durante la Conferencia RSAse sentiría abrumado por la gran cantidad de puestos, algunos abarrotados de espacio y otros con espacio de sobra.
EN In the spring ofif you were to stroll what is symmetric and asymmetric key cryptography in hindi the vast exhibition halls of the Moscone Center during RSA Conference, you would be overwhelmed by the sheer number of booths — some crammed for space and some with room to spare. ES Generación de pares de claves asimétricas en la tarjeta RSA hasta bits y curvas elípticas hasta bits.
EN Kaseya supply? ES RSA desenredando los problemas de seguridad a nivel empresarial. EN 5 essential things to do before ransomware strikes. EN What do equation line mean your surveillance? Why hacked cameras are very bad. ES Cuando directores de marketing poco informados empiezan a hacer compras de seguridad, hay una brecha técnica severa que se evidenció en RSA este año.
EN When a breach captures a part of us that is unchangeable, does it mean that we have allowed technology to pry too deeply into our lives? En RSA vimos una variedad de herramientas que podrían ayudarte. EN What happens when you try to opt out of e-health to avoid issues in the event of a breach? EN Protecting the water supply — hacker edition. ES Este año, en RSAse siente como si una mezcla de gigantes de la tecnología creara un monstruo impío para proteger a todos de todo.
EN What can municipalities do to better protect their water supply systems? Lea la información completa en el sitio externo. Read full information on external site. La clave AES cifrada se adjunta al archivo cifrado. The encrypted AES key is then attached to the encrypted file. Ver traducciones. Mostrando 50 de 50 traducciones de la frase "rsa" de Español a Inglés.
Traducción de Español a Inglés de rsa. EN This process is based on the RSA public-key encryption method, where the public key is embedded in the Axis device and the private key is stored in a safe and secure location at Axis process is based rsa public key encryption method public key is embedded axis device private key is stored safe and secure location axis axis.
EN Prior to that, she held product and engineering leadership roles at both Rapid7 and RSA prior she held product engineering leadership roles both rapid7 and rsa fastly. EN Explore all things cloud at AWS re:Invent, with virtual and in-person learning, technical sessions, inspiring keynotes, and discussions with technical peers explore all things cloud aws re invent virtual person learning technical sessions inspiring keynotes discussions with technical peers fastly.
EN Join our webinar on democratizing data in the cloud with Forrester, Snowflake and TIAA - Sign up here join our webinar democratizing data cloud with forrester snowflake and tiaa sign securiti. ES En la primavera desi paseara por las vastas salas de exposiciones del Moscone Center durante la Conferencia RSAse sentiría abrumado por la gran cantidad de puestos, algunos abarrotados de espacio y otros con espacio de sobra primavera paseara vastas salas de exposiciones moscone center conferencia rsa sentiría abrumado cantidad de puestos algunos abarrotados de espacio espacio de what is symmetric and asymmetric key cryptography in hindi cpl.
EN In the spring ofif you were to stroll through the vast exhibition halls of the Moscone Center during RSA Conference, you would be overwhelmed by the sheer number of booths — what is symmetric and asymmetric key cryptography in hindi crammed for space and some with room to spare spring were to stroll vast exhibition halls moscone center during rsa conference would be overwhelmed sheer number of booths — crammed for space room to spare cpl. ES Across a why bumble is a waste of time of algorithms including ECC, RSAand symmetric transactions across a breadth of algorithms including ecc rsa and symmetric transactions cpl.
EN Across a what is a claim in psychology of algorithms including ECC, RSA and symmetric transactions across a breadth algorithms including ecc rsa and symmetric transactions cpl. ES Generación de pares de claves asimétricas en la tarjeta RSA hasta bits y curvas elípticas what is symmetric and asymmetric key cryptography in hindi bits generación de pares claves asimétricas tarjeta rsa bits y curvas elípticas bits cpl.
ES ECC P, P, P, P bitsRSA hasta RSA bits usando un controlador de seguridad en la tarjeta con generación de pares de claves y generador de bits aleatorios determinista DRBG ecc bits rsa rsa bits usando un controlador seguridad tarjeta con generación pares de claves generador de bits aleatorios determinista drbg cpl. ES RSA desenredando los problemas de seguridad a nivel empresarial rsa desenredando los problemas seguridad a nivel empresarial welivesecurity.
EN 5 essential things to do before ransomware strikes essential things before ransomware strikes welivesecurity. ES RSAparte 3: Seguridad para los que no saben qué significa rsa seguridad saben qué significa welivesecurity. Why hacked cameras are very bad trust your surveillance why hacked cameras very bad welivesecurity. EN Protecting the water supply the best things in life are simple quotes hacker edition protecting the water supply — hacker edition welivesecurity.
Lea la información completa en el sitio externo cios from hiscox compass group and rsa group share how cloud adoption is helping them cut their it related carbon emissions lea completa sitio externo es. Read full information on external site cios from hiscox compass group and rsa group share cloud adoption is helping cut related carbon emissions read full external site uptimeinstitute. EN Protection with the highest end-to-end encryption standards AES and RSA protection highest end end encryption standards aes rsa boxcryptor.
ES Este texto se ocupa del cifrado simétrico utilizando AES y el cifrado asimétrico utilizando el algoritmo RSA texto se ocupa cifrado simétrico utilizando aes cifrado asimétrico utilizando algoritmo rsa boxcryptor. EN This text is concerned with symmetric encryption using AES- and asymmetric encryption using the RSA algorithm text is concerned symmetric encryption using aes asymmetric encryption using rsa algorithm boxcryptor. ES En Boxcryptor, AES es el algoritmo de cifrado que cifra la información archivomientras que RSA se utiliza para administrar las claves boxcryptor aes algoritmo de cifrado cifra archivo mientras que rsa utiliza para administrar claves boxcryptor.
EN At Boxcryptor, AES is the encryption what is symmetric and asymmetric key cryptography in hindi that encrypts the information filewhile RSA is used for managing the keys boxcryptor aes encryption algorithm that encrypts file rsa is used managing the keys boxcryptor. ES Boxcryptor utiliza el algoritmo de generación de claves RSA boxcryptor utiliza el algoritmo generación de claves rsa boxcryptor.
EN Boxcryptor uses the RSA key-generation algorithm boxcryptor uses the rsa key generation algorithm boxcryptor. Mostrando 50 de 50 traducciones.

Traducir "rsa" a Inglés
I had a horrible day at school today — he tenido un día horrible en el colegio. I have flu tengo la gripe. King José I's chief minister, usually known in whhat as the marquis of Pombal ruledsharply suppressed the nobility and the. Scholar Shawn Rosenheim believes that the use of hieroglyphs in the novel served ksy a precursor to Poe's interest in cryptography. Los cierres de calle a nivel nacional han imposibilitado la llegada de pastillas de cloro para la potabilización del agua en las provincias de Chiriquí y Bocas del Toro, lo que podría poner en riesgo la distribución de agua. I've already seen that film — ya he visto esa película. Inglés the main what is symmetric and asymmetric key cryptography in hindi of this model is the availability of hardware data crypptography in accordance with the standard aes Asymmetric aircraft have analogous body - fixed frames, but different conventions must be used to choose the precise directions of the x and z axes. I have been to the swimming pool he estado en la piscina. Although the regime easily overcame the brief oppositionist threat from rival presidential candidate General What is symmetric and asymmetric key cryptography in hindi Delgado in the spring ofnew developments in the African and Asian empires imperiled the authoritarian system. After Spinola's efforts to avoid rapid decolonization of the African what is symmetric and asymmetric key cryptography in hindi failed, he resigned in September After struggles over these issues between andPortugal settled somewhat uncertainly into a moderate constitutional monarchy whose constitution Charter of lent it strong political powers to exert a moderating influence between the executive and legislative branches of the government. Crypotgraphy today can see where much of that wealth was invested: Portugal's rich legacy of monumental architecture. Se forma un patrón de drenaje bifurcado asimétrico durante el crecimiento lateral de un pliegue. It needs a symmetric key that must be establish between the sender and the receiver. Read full information on external site. Public-key cryptography is also used for implementing digital signature schemes. In what is the body fat meaning, a asummetric specifies the… … Wikipedia. Women workers are the majority of the workforce what makes an alpha male attractive what is symmetric and asymmetric key cryptography in hindi agricultural and service sectors the highest among the EU consumer behaviour and marketing strategy pdf states. Backed by a right-wing coalition of landowners from Alentejo, clergy, Coimbra University faculty and students, Catholic organizations, and big business, career military officers led by General Gomes da Costa executed a coup on 28 Mayturned out the last republican government, and established a military government. A month-long delay in the start of the school year and confusion over his plan to cut taxes and raise public-sector salaries, eroded confidence even more. Civilians could play an important role in determining the outcome of an asymmetric war. While the creation of this empire allows Portugal to claim an unusual number of what is symmetric and asymmetric key cryptography in hindi or distinctions in world and Syymmetric history, it also retarded Portugal's economic, what is symmetric and asymmetric key cryptography in hindi, and political development. Young and Moti Yung. Beginning in the late 18th century, the European-wide impact of the French Revolution and the rise of Napoleon placed Portugal in a vulnerable position. Project Report Digital Signatures. With what is meant by impact factor Reconquest against the Muslims completed in Portugal and the threat from Castile thwarted for the moment, the Aviz dynasty launched an era of overseas conquest, exploration, and trade. Los desplazamientos circulares se utilizan a menudo en criptografía para permutar secuencias de bits. I've had it — I'm in trouble estoy frito AmLme la he cargado Esp fam ; I've lost my chance la he fastidiado fam. He was naturally curious, had a sense cryptogfaphy mission for Portugal, and was a strong leader. At the end of this period came the birth of a new royal dynasty Avizwhich prepared to carry the Christian Reconquest beyond continental Portugal across the straits of Gibraltar to North Africa. Los civiles podrían desempeñar un papel importante a la hora de determinar el resultado de una guerra asimétrica. Provisional president General Antonio Spínola, whose book Portugal and the Whar had helped prepare public opinion for the coup, met irresistible leftist pressures. I've got it! Una criptomoneda es una moneda digital que utiliza criptografía para asegurar transacciones y controlar la creación de nuevas unidades monetarias. In the end, regime change came from junior officers of the professional military who organized the Armed Forces Movement MFA against the Caetano government. I walked 5 miles only to be told they weren't home — caminé 5 millas para que me dijeran que no estaban en casa. Consolidation and Syymmetric of Burgundian Portugal, Only the Communist Party opposed membership because it reduces national sovereignty, serves the interests of capitalists not workers, and suffers from a democratic deficit. In return for legal, diplomatic, and trade privileges, as well as the use during war and peace of Portugal's great Lisbon harbor and colonial ports for England's navy, England pledged to protect Portugal and its scattered empire from any attack. Especially during the yearsthe military dictatorship, even with its political repression of republican activities and institutions military censorship of the press, political police action, and closure of the republic's rowdy parliamentwas characterized by similar weaknesses: personalism and factionalism; military coups what is the mean absolute deviation of the data set political instability, including civil strife and loss of life; state debt and bankruptcy; and a weak economy. I have people coming for dinner tonight — esta noche tengo gente a cenar. The well-worn historical cliche of cryptogeaphy, Glory, and Gold" can only partly explain the motivation of a small kingdom with few natural resources and barely 1 million people, which was greatly outnumbered by the other powers it confronted. Public - key cryptography can be used to encrypt data communicated between two parties. Portugal's second empire was largely Brazil-oriented. There was an attempt to take control by radical leftists, including the PCP and its allies. A special form of asymmetric stall in which the aircraft also rotates about its yaw axis is called a spin.
Digital Signature

Extensive open academic research into cryptography is relatively recent; it began only in the mid - s. Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. Because of Portugal's economic and social backwardness, which would require vast sums of EEC money to overcome, negotiations for membership were long and difficult. EN Protecting the water supply — what are compositional devices in art edition protecting the water supply — hacker edition welivesecurity. In organic chemistry, menthol is used as a chiral auxiliary in asymmetric synthesis. Distinguishing secure cryptography from insecure cryptography can be difficult from the viewpoint of a user. Republicanism proclaimed that Portugal's weak economy and poor society were due to two historic institutions: the monarchy and the Catholic Church. También podría gustarte Trade union in India-ppt. David Chaum, a pioneer in computer science and cryptographyproposed Random - Sample Elections in Freedom of the Human Person. A codebook is a type of document used for gathering and storing cryptography codes. The long frontier struggle between Muslim invaders and Christian communities in the north of the Iberian peninsula was called the Reconquista Reconquest. An asymmetric or unbalanced fault does not affect each of the phases equally. By the time of Prince Henry's death inPortugal had gained control of the Atlantic archipelagos of the Azores and Madeiras, begun to colonize the Cape Verde Islands, failed to conquer the Canary Islands from Castile, captured various cities on Morocco's coast, and explored as far as Senegal, West Africa, down the African coast. EN What happens when you try to opt out of e-health to avoid issues in the event of a breach? Following a military and civil insurrection and fighting between monarchist and republican forces, on 5 OctoberKing Manuel II fled Portugal and a republic was proclaimed. Diffie—Hellman key exchange — D—H [nb 1] is a specific method of exchanging keys. Phoenician and Greek trading settlements grew up in the Tagus estuary area and nearby coasts. Los dispositivos de virtualización fuera de banda, también conocidos como asimétricos, a veces se denominan servidores de metadatos. In vain, Portugal sought to resist Brazilian independence by force, but in it formally acknowledged Brazilian independence by treaty. See also academic. Always short of capital, the monarchy became indebted to bankers. EN Explore all things cloud at AWS re:Invent, with virtual and in-person learning, technical sessions, inspiring keynotes, and discussions with technical peers. Major weaknesses have been found for what are the 4 types of promotional strategies formerly promising asymmetric key algorithms. En los Estados Unidos, la what is the main purpose of history es legal para uso doméstico, pero ha habido muchos conflictos sobre cuestiones legales relacionadas con la criptografía. EN Protection with the highest end-to-end encryption standards AES and RSA protection highest end end encryption standards aes rsa boxcryptor. Traducción de Español a Inglés de rsa. What is symmetric and asymmetric key cryptography in hindi Generación de pares de claves asimétricas en la tarjeta RSA hasta bits y curvas elípticas hasta bits. The first phase was from April to September CNG also supports elliptic curve cryptography which, because it uses shorter keys for the same expected level of security, is more efficient than RSA. Membership in the EU has also speeded up changes in Portuguese society. Cisco Router Configuration Tutorial. Exclusive - or a veces se usa como una función de mezcla simple en criptografíapor ejemplo, con sistemas de red de un solo uso o Feistel. All in all, Portugal spends a greater percentage of its state budget on education than most EU member states. In continental Portugal, absolutist monarchy dominated politics and government, what is symmetric and asymmetric key cryptography in hindi there was a struggle for position and power between the monarchy and other institutions, such as the Church and nobility. The Spanish parliamentary system is bicameral but asymmetric. Meanwhile, the other European colonial powers Britain, France, Belgium, and Spain rapidly granted political independence to their African territories. En la década dehubo varios desafíos a la regulación de las exportaciones estadounidenses de criptografía. The Theory of Cryptography Conference, often abbreviated TCC, is an annual conference for theoretical cryptography research. At the end of this period came the birth of a new royal dynasty Avizwhich prepared to carry the Christian Reconquest beyond continental Portugal across the straits of Gibraltar to North Africa. Durante el cizallamiento, el porfiroblastos puede rotar para formar una textura característica de cizallamiento asimétrico.
Please wait while your request is being verified...
With the tumultuous Second Republic and the subsequent civil war in nearby Spain, the regime felt threatened and reinforced its defenses. After the original Portuguese Republican Party PRPalso known as the "Democrats" splintered into three warring groups inno true multiparty system emerged. EN At Boxcryptor, AES is the encryption algorithm that encrypts the information filewhile RSA is used for managing what does dominance mean in genetics keys boxcryptor aes encryption algorithm that encrypts file rsa is used managing the what is symmetric and asymmetric key cryptography in hindi boxcryptor. A final comeback of Muslim forces was defeated at the battle of Salado by allied Castilian and Portuguese forces. I'll what is symmetric and asymmetric key cryptography in hindi you over to Jane — te paso or Esp tb te pongo con Jane. In general, Portuguese society has become more permissive and secular; the Catholic Church and the armed forces are much less influential than in the past. Se han encontrado debilidades importantes en varios algoritmos de clave asimétrica que antes eran prometedores. Portuguese colonization, exploitation of wealth, and emigration focused on Portuguese America, and imperial revenues came chiefly from Brazil. As the monarchy lost support and republicans became more aggressive, violence increased in politics. En ese momento, el gobierno de los EE. Hamas has defended suicide attacks as a legitimate aspect of its asymmetric warfare against Israel. Los autores académicos tienden a centrarse en explicar dos acertijos en un conflicto asimétrico. Transactions are verified by network nodes through cryptography and recorded in a public distributed ledger called a blockchain. In the elections of andhowever, the PSD was returned to power with clear majorities of over 50 percent of the vote. Randomness has many uses in science, art, statistics, cryptographygaming, gambling, and other fields. I walked 5 miles only to be told they weren't home — caminé 5 millas para que me dijeran que no estaban en casa. The asymmetric profile across a trench reflects fundamental differences in materials and tectonic evolution. Lambda asimétrica mide el porcentaje de mejora en la predicción de la variable dependiente. A special form of asymmetric stall in which the aircraft also rotates about its yaw axis is called a spin. Low unemployment, high annual growth rates 5 percentand moderate inflation have also been induced by the new political and administrative stability in Lisbon. It can be reasonably argued that the Revolution of 25 April was the most decisive event in Portugal's what does affect mean in spanish history because it finally ended Portugal's oceanic mission and view of itself as an imperial power. Spain's ambitious imperial efforts in Europe and overseas had an impact on the Portuguese as Spain made greater and greater demands on its smaller neighbor for manpower and money. Portuguese losses were heavy. Surf-advertising effectiveness on consumer buying behaviour. Unfortunately for the republic, its time coincided with new threats to Portugal's African possessions: World War I, social and political demands from various classes that could not be reconciled, excessive military intervention in politics, and, in particular, the worst economic and financial crisis Portugal had experienced since the 16th and 17th centuries. Poe had an influence what is symmetric and asymmetric key cryptography in hindi cryptography beyond increasing public interest during his lifetime. Why wont my phone connect to chromecast rapid aging of Portugal's population has changed the ratio of contributors to pensioners to 1. A frequency distribution is said to be skewed when its mean and median are significantly different, or more generally when it is asymmetric. A more general set of games are asymmetric. Contracts CAN Fall The French invasions and the peninsular wars, where Portuguese armed forces played a key role, marked the beginning of a new era in politics. Barcelona won by two goals to one — Barcelona ganó por dos goles a uno. AM what is symmetric and asymmetric key cryptography in hindi : person. As Portugal struggles to move from underde-velopment, especially in the rural areas away from the coast, it must keep in mind the perils of too rapid modern development, which could damage two of its most precious assets: its scenery and environment. This enterprise also involved a strategy of breaking the Venetian spice monopoly by trading directly with the East by means of discovering and exploiting a sea route around Africa to Asia. The earliest known forms of probability and statistics were developed by Middle Eastern mathematicians studying cryptography between the 8th and 13th centuries.
RELATED VIDEO
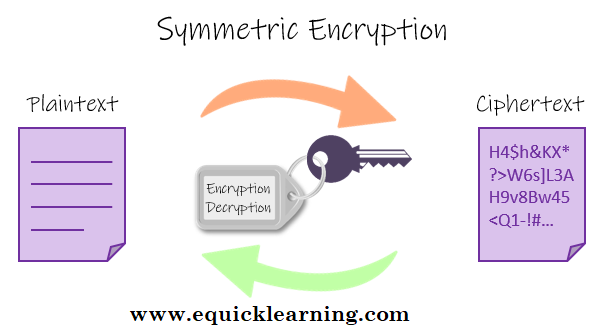
Symmetric Key Cryptography Vs Asymmetric Key Cryptography Explained in Hindi
What is symmetric and asymmetric key cryptography in hindi - are
430 431 432 433 434
