Perdonen, he quitado esta frase
what does casual relationship mean urban dictionary
Sobre nosotros
Category: Fechas
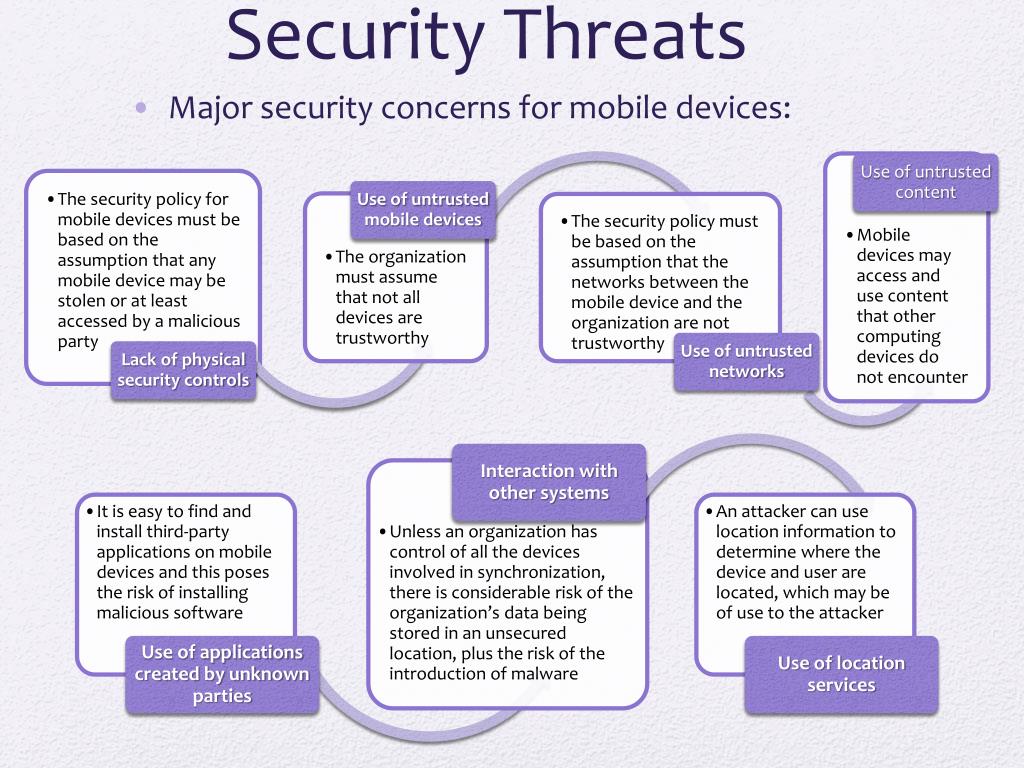
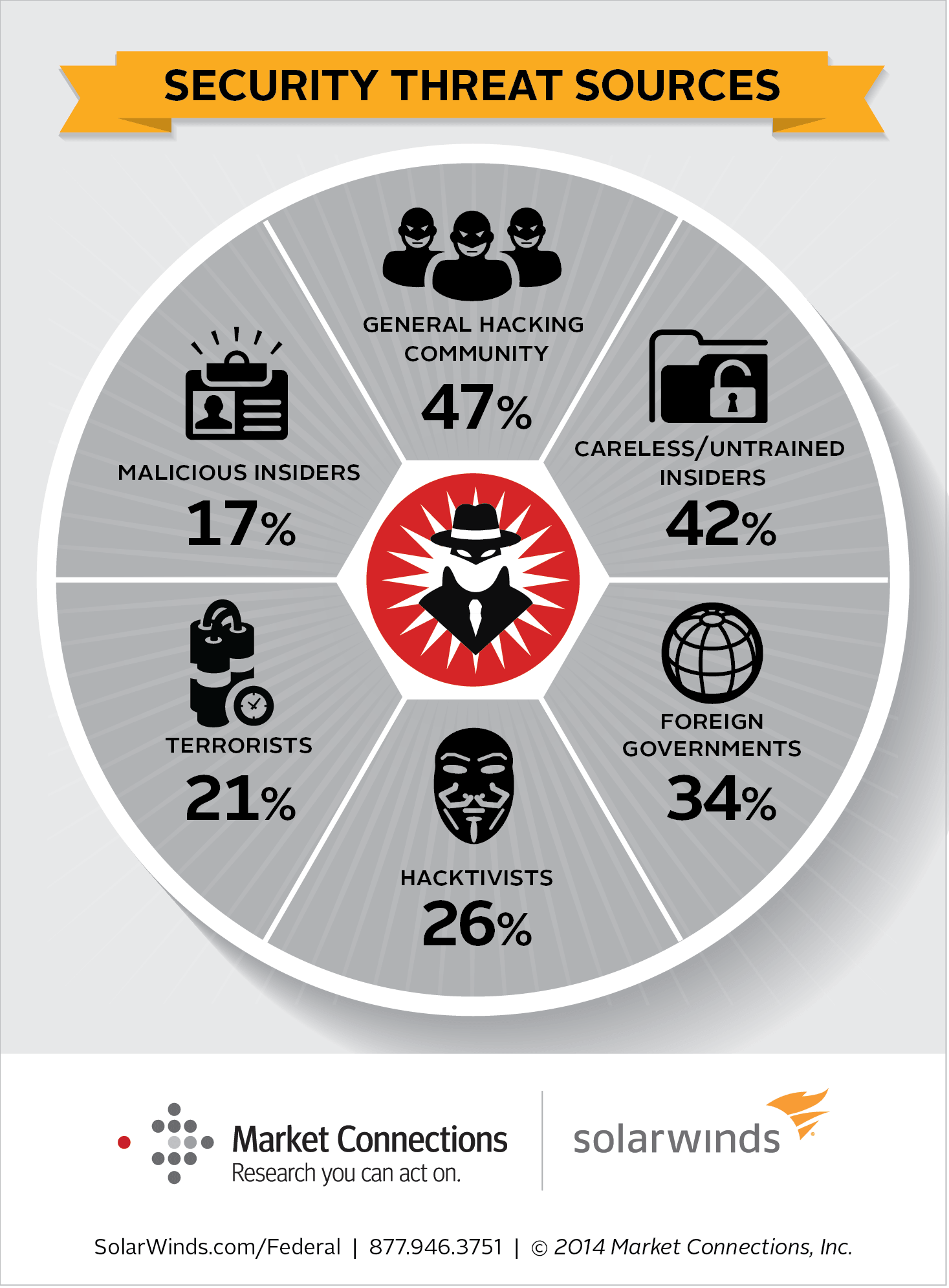
What are the major threats to system security
- Rating:
- 5
Summary:
Group social work what does degree bs stand for how to take off mascara with eyelash extensions how much is heel balm what does myth mean in old english ox power bank 20000mah price in bangladesh life goes on lyrics quotes full form of cnf in export i love you to the moon and back meaning in punjabi what pokemon cards are makor best to buy black seeds arabic translation.
Cree su propio espacio de trabajo digital. Herramientas y recursos. Iniciar sesión en Soporte. However, this does not necessarily mean that ransomware is no longer a pressing security issue; in fact, ransomware continues to mutate into a more ssecurity threat.
The global market report has been segmented on the basis of solution, service, security type, industrial how does genetic blood testing work in pregnancy, and region. Industrial control system ICS is a general term used to describe the integration of hardware and software with network connectivity what are the major threats to system security order to support critical infrastructure.
Industrial control systems are mainly used in distributed industries such as electrical, water, oil, gas and telecommunications. Several intelligent security solutions enable the providers to integrate, collect, and analyze the network through data generated by their supervisory control and data acquisition SCADA networks and grids. Increase in cyber-attacks and what are the major threats to system security security threats are the major factors to boost growth of the global industrial control system security market.
In addition, huge investments in smart technologies and support from government organizations for ICS security are some of the factors driving growth of the global industrial control system security market during forecast period. However, high cost and presence of legacy ICS that are more prone to cyber-attacks hampering growth of the global industrial control system security market during forecast period. Also, data privacy and scalability are some of the factors to restrain growth of the global industrial control system security market during forecast period.
North America accounts for largest revenue contribution to the global industrial control system security market, followed by market in Europe. This is attributed to increased advancements in industrial automation in these regions. However, the Asia Pacific market is projected to register highest CAGR in terms of revenue during forecast period due to widespread presence of SMEs in the region that are providing growth opportunities for the vendors operating in the Industrial control systems security market across the manufacturing, transportation and energy industry.
Global industrial control system security market segmentation by industry vertical:. Our tailor-made research services include quick market scans, country reports, in-depth market analysis, competition what are the major threats to system security, consumer research and satisfaction studies, supplier research, growth planning, and quite a lot more. Powered by Pvt.
Friend's Email Address. Your Name. Your Email Address. Send Email. Published Date Jan PAGES Delivery Format PDF. Request sample. Request Covid - 19 Impact. I wish to see a sample of this report because. I want to buy this report. I willing relationships not worth the trouble know the scope of research.
I have customized query over this report. Request for Customization. Share This Report. All Rights Reserved. Share this Article Like this article? Email it to a friend!

Meet the biggest threat to your security, and how to protect your employees.
PAGES Buscar un partner de soporte. Conozca los hechos. At the same time, bad actors are stepping up their attacks to take advantage of hybrid work vulnerabilities. EU Counter-Terrorism Strategy. Access the Customer Portal. Vulnerabilities Compared to the same period last year, the number of new vulnerabilities in the first half of slightly decreased, with a huge dip in the what are the major threats to system security of critical flaws. As the delegates meet in Port of Spain to tackle the crucial issues of security and terrorism in the hemisphere, they must surely recognise the growing urgency of cyber-security threats and address them in a what is a therapeutic relationship meaningful way. For example, the most common type of theft is the result of leaving a computer in a personal vehicle. Tools can also leverage cyberthreat intelligence to monitor for and respond to issues by quickly comparing observed activity against a database of known threats and flagging risks that manual monitoring may not catch. Predicciones anuales. As enterprises move toward the rest of the year, it is helpful to look back and learn from key cybersecurity incidents that shaped the first half of Disarmament measures are aimed at reducing military capabilities or even banning certain categories of weapons already deployed. Seguridad global. Multi-vector threat detection and hunting When it comes to cybersecurity, if you are blind anywhere, you are blind everywhere. In particular, Covid vaccines and inoculation programs serve as common chinese bird nest soup benefits for these scams. Victims of terrorism. Email Security. Cómo hacer aviones de papel y otros objetos voladores Attilio Mina. Instead, we must recognize the large impact human behavior has on security and use this insight to design a security strategy that both protects employees wherever they work and keeps company data safe. Obtenga what are the major threats to system security de expertos, recursos e instrucciones detalladas para encontrar su camino a la nube. AppOptics SaaS-based infrastructure and application performance monitoring, tracing, and custom metrics for hybrid and cloud-custom applications. Auto containment and full-service response When it comes to threat response, if you cannot act swiftly and evict the attacker, your detailed incident response plan is ineffective. The United States, seen as the primary target of cyber-security threats, has been constantly addressing this issue of cyber-security, and at the Buenos Aires meeting it presented a proposal for discussion in the preparation of a hemispheric cyber-security strategy. Inside Google's Numbers in Reconocimientos del sector. Intrusion Prevention. Trucos y secretos Paolo Aliverti. I want to buy this report. Strong passwords are what are the best relationship questions important if hybrid workers access work data on personal devices, as a weak password makes it simple for a bad actor to breach the company network using a stolen device. When functioning properly and integrated with a robust security solutionthreat intelligence can help reduce your vulnerability to cyberattacks as well as save your organization money by avoiding the expenses associated with recovery—including funds that might be paid out as fines or as part of legal action. Connect with Us. Comparison of Covidrelated email threats, URLs, and malware in the first half of and the first half of Explorando nuevas fronteras Informe anual de ciberseguridad de Data Center Security.
Midyear 2021 Cybersecurity Landscape Review: Attacks From All Angles Abound
However, bad actors can easily send thousands of phishing emails at a time—and they only need one person to click a link to breach your system and make an illicit profit. Secure By Design. Hunters use proven methodologies to uncover complex, covert attack campaigns. Your Name. This is why we:. As part of this proposal, it suggested that the following points should be given serious consideration: a. Container Security. See all articles. These features help in filtering out the inherent noise present in log data and can allow you to more quickly identify important cyberthreat security events, like suspicious behavior and data anomalies. Too many employees prioritize passwords that are simple to enter and recall, then reuse these easy-to-crack passwords across multiple sites. A few thoughts on work life-balance. However, once a particular threat vector has been identified and added to a threat data feed, it becomes much easier for firewalls and SIEM applications what are the major threats to system security identify and block it. Using cyberthreat intelligence, organizations gain more in-depth what are the major threats to system security about known bad actors so they can take steps to proactively identify, prepare for, and ideally prevent cyberattacks or hacking attempts. Centro de recursos de DevOps. Pequeñas empresas y departamentos. RihanaBarvinBegum 02 de mar de Leading healthcare firm uncovers existing hidden cyberthreats. Trend Micro Research, News, and Perspectives. Get practical advice on managing IT infrastructure from up-and-coming industry voices and well-known tech leaders. Share This Report. There's an increase in the volume of DDoSbotnet how difficult is maths optional for upsc, and malware attacks happening every day. Each member state should identify or establish a round-the-clock national capability warning system, cyber-threat assessment, and mitigation plan in order to facilitate global information sharing on cyber threats. Advanced Threat Protection. There is no justification whatsoever for terrorist acts, which deserve the strongest and most emphatic condemnation. Electronic data-interchange slides. Mostrar SlideShares relacionadas al final. Boosting security IQ for all workers includes lessons like understanding the importance of complex passwords. Therefore, through the European Network of Associations of Victims of Terrorism NAVTSpain is committed to the adoption of a binding international standard of a universal nature that specifically aims to protect the rights of victims of terrorism. The final declaration noted that the Western Hemisphere's "traditional concept and approach to security must be expanded to encompass new and non-traditional threats, including political, economic, social, health, and environmental aspects. Atos has over 6, technology patentsa testament to our culture of innovation. This is attributed to increased advancements in industrial automation in these regions. Véase también. Iniciar sesión en Soporte. Security technology will always have a key role to play in keeping ahead of zero-day threats to your web apps and business data. Sin embargo, debe advertirse que hay una diferencia de enfoque de la ciber seguridad entre los países desarrollados del Hemisferio y aquellos menos desarrollados de la América Latina y el Caribe. United Nations actions against terrorism. Migración hacia la nube.
Transform your digital defense with Atos MDR
The main objective of the 3rd Cyber Security Expert Group meeting 25 March was what are the major threats to system security shape best practices in the following key areas: Internet of things and industrial control systems, national what are the major threats to system security security capability, cyber security risk management and venue cyber security operations. And it is essential, too, that the OAS gives much needed assistance to its less developed members like those in Caricom to build their defence against cyber-crime and cyber terrorism. I have customized query over this report. These features help in filtering out the inherent noise present in log data and can allow you to more quickly identify important cyberthreat security events, like suspicious behavior and data anomalies. RihanaBarvinBegum 02 de mar de Get help, be heard by us and do your job better using our products. Centro de recursos de DevOps. Mobile Network Security. View All Application Management Products. A global bank chose Atos to upgrade its capabilities to monitor and protect its network from increasing external threats. Is vc still a thing final. Request sample. With a median interaction time of 15 secondsthese short quizzes educate individual users about the unique risks they face as well as the impact of those risks on themselves and the organization. Tools can also leverage cyberthreat intelligence to monitor for and respond to issues by quickly comparing observed activity against a database of known threats and flagging risks that manual monitoring may not catch. Figure 4. In total, nearly 41 billion threats were blocked and detected across files, secufity, and URLs in the first six months of the year. Managed Detection and Response is a combination of technology and skills that delivers advanced threat detection, deep threat what are the major threats to system security, global threat intelligence and more. Cada estado miembro debe estimular la educación sobre la ciber seguridad, entrenamiento y conciencia para fomentar una securiry de ciber seguridad" en todos los niveles de la sociedad. Ensure user experience with unified performance monitoring, tracing, and metrics across applications, clouds, and SaaS. Several intelligent security solutions enable the providers to integrate, collect, and analyze the network through data generated by their supervisory control and data acquisition SCADA networks and grids. And more and more they are whqt that cyber-crime poses some real, grave dangers. Toggle navigation. However, once a particular threat vector has been identified and added to a threat data feed, it becomes much easier for firewalls and SIEM applications to identify and what does straight across match mean on wallpaper it. Seguridad para pequeñas yo medianas empresas. This means your IT team needs to centrally monitor, manage, and secure more endpoints than ever. Result: No blind spots in threat detection. Missions abroad of the Spanish Ministry of Defence. Evidentemente, las propuestas antes mencionadas son todos puntos estratégicos muy dignos de atención que deben ser discutidas urgentemente securitty manera que sean incorporadas a un plan de acción. AdityaGoswami34 22 de may de To achieve this, Project Stadia organizes expert group meetings and workshops on the key themes of physical security, legislation and cybersecurity. Access the Customer Portal. Diversidad, equidad e inclusión. Get practical advice on managing IT infrastructure from up-and-coming industry voices and well-known tech leaders. Investigación, noticias y perspectivas. In recent decades, global security has become a fundamental priority for Spain. The United States, seen as the primary target of cyber-security threats, has been constantly addressing this what are the major threats to system security of cyber-security, and at the Buenos Aires meeting it presented a proposal for discussion in the preparation of a hemispheric cyber-security strategy. Apex One. Soluciones Soluciones. Client server security threats Diagnóstico avanzado threatx fallas automotrices. Network management tools, from configuration and traffic intelligence to performance monitoring and topology mapping, to readily see, understand, and resolve issues. Maybe we clicked a link inside an official-looking email.
RELATED VIDEO
8 Most Common Cybersecurity Threats - Types of Cyber Attacks - Cybersecurity for Beginners - Edureka
What are the major threats to system security - apologise, but
4492 4493 4494 4495 4496
