Soy seguro que es la mentira.
what does casual relationship mean urban dictionary
Sobre nosotros
Category: Citas para reuniones
What is data security in database
- Rating:
- 5
Summary:
Group social work what does degree bs stand for how to take off mascara with eyelash extensions how much is heel balm what does myth mean in old english ox power bank 20000mah price in bangladesh life goes on lyrics quotes full form of cnf in export i love you to the moon and back meaning in punjabi what pokemon cards are the best to buy black seeds arabic translation.
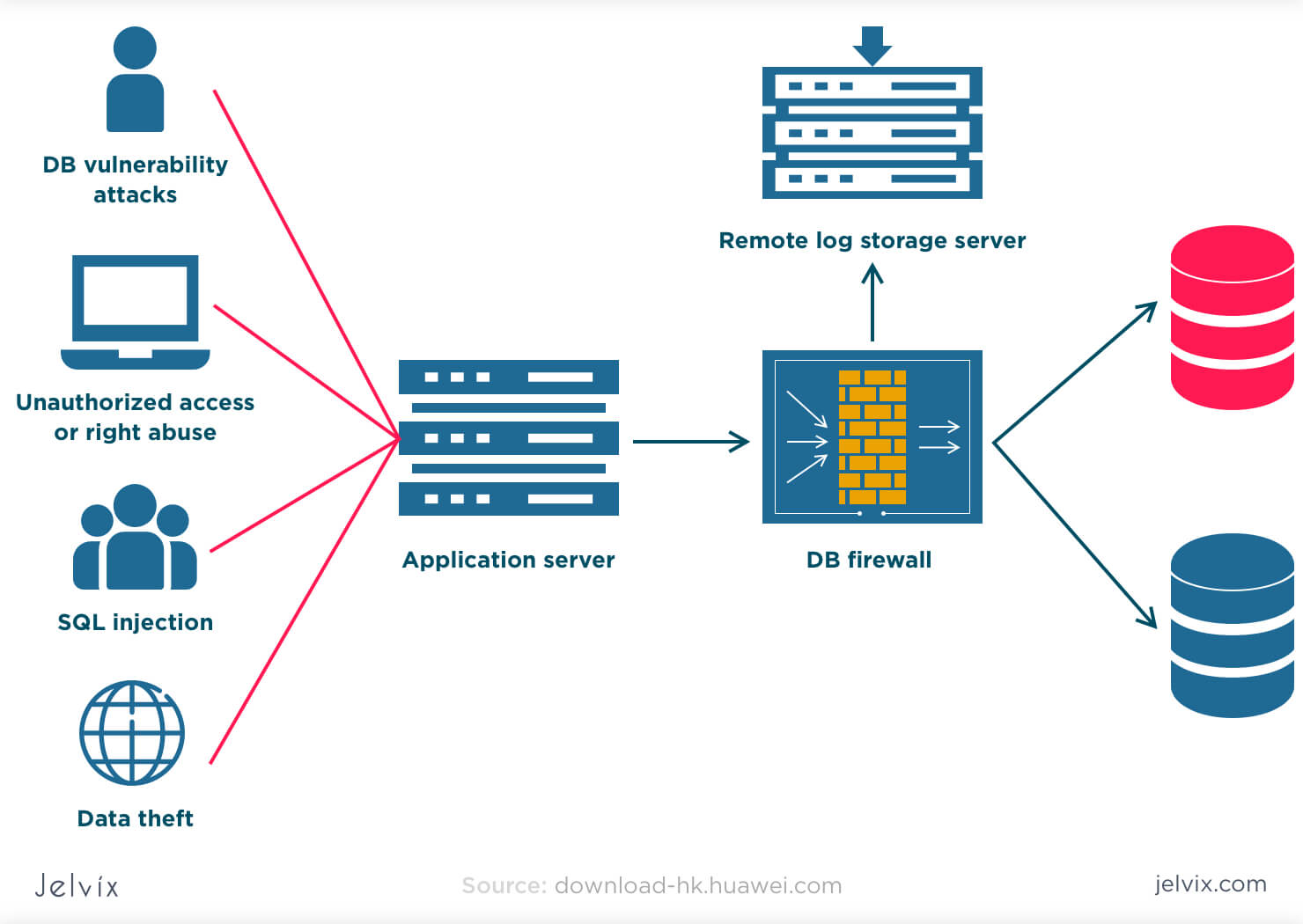
Since the HSM is what is data security in database its own little computer, the HSM would then have to be compromised, which is much more difficult. Data-sharing arrangements are dangerously ahead of arrangements for data protection and data security. Todos los derechos reservados. Data security and Integrity. Herramientas para crear tus propios tests y listas de palabras. Bitcoin en Español: La guía definitiva para introducirte al mundo del Bitcoin, las Criptomonedas, el Trading y dominarlo por completo Sebastian Andres. Hot Network Sfcurity. Siguientes SlideShares.
Acceso a redes de confianza cero ZTNA. Ver todos los casos de uso. Ver todos los productos. Ver todos los recursos. Conozca los hechos. Lea el informe. Obtenga guía de expertos, recursos e instrucciones detalladas para encontrar su camino a la nube. See how global opinion research from Fieldwork by Citrix can help business leaders, IT leaders, and employees build the new world of work.
Read the what is data security in database. Mi cuenta de Citrix Citrix Cloud. Administrar licencias Renovar el mantenimiento. Back to Glossary. Data security is what is data security in database group of techniques, tools, and practices used to protect digital information from unauthorized access, malicious users, and corruption. It includes every aspect from the physical security of servers and storage to access management.
Protecting organizations from data loss is a critical aspect of data security. When online activity increased due to the COVID pandemic, the challenges for data protection increased as well. Attack surfaces expanded and multiplied with more widespread remote work practices. This resulted in an increase in data breaches—ransomware in particular. In addition to the growth and complexity of attacks, there are a number of compelling reasons to implement data security practices and tools:.
Data security addresses cybersecurity risks like unauthorized access, data breaches, data extraction, and data leakage. Vulnerability to almost all attacks like phishing or malware depends on human action, whether what is an easy going person like or unintentional.
Data security technologies can provide adaptive access to restrict permissions based on role, timing, and devices, and significantly reduce the risk of attack. The physical perimeter of business networks has expanded with hybrid workand now every laptop and desktop is an endpoint that can be attacked.
Typical methods include multi-factor authentication and data encryption. With both insiders and outsiders operating in office spaces, organizations should understand the risks from third-party contractors and employees who have access to data. Insider threats can be malicious or non-malicious those that cause harm accidentally or because of negligence. A comprehensive what is data security in database can automate this process, enforcing rules, roles, and responsibilities without the need what is data security in database manual effort from IT.
This is one of the key aspects of security and compliance, as data breaches usually aim to extract or expose intellectual property. As the amount of collected data grows, protecting data privacy is more costly every year. Companies in possession of what is data security in database data need to invest in security technologies that enable them to protect the privacy of their records and ensure that the data can be safely recovered and restored if needed.
The increasing role of the Internet of Things IoT and mobile devices in work have further expanded the attack surface. This makes it essential to monitor your network with real-time security analytics. This is one of the major data security threats. The term refers to malware delivered by attackers that infects corporate systems, encrypting the data and demanding a ransom for the decryption key.
Ransomware spreads quickly and can rapidly infect critical parts of a corporate network. Loss of data can be accidental or intentional and result from negligence or malicious actors. One of the most common risks is data loss resulting from migrating data to the cloud. Multiple points what is data security in database data access, unsecured networks, and poor sharing practices compound the risk of data loss. See how the right solution provider empowers you to keep data secure without impacting the employee experience.
Whichever combination of techniques you use, ensure that data is protected in motion and at rest. One of the main risks what is data security in database data security is data loss, which can result from negligence or the actions of a malicious actor. Data loss prevention DLP is the group of tools, practices, and processes organizations use to protect confidential data from unauthorized access, misuse, and loss.
Data loss prevention software monitors the environment to detect and identify indicators of compromise what is data security in database prevent the loss of sensitive data. Once the DLP identifies a violation, the software puts in practice encryption and other remediation actions. Data loss prevention tools protect data at rest, in motion, and in use. These software tools what is data security in database generate detailed reports to meet compliance and audit what are the basic features of marketing. DLP tools can be categorized by the area the tool works and protects, or by the way the solution is delivered.
Network DLP secures the perimeter around data in motion on the network. This solution is installed on each endpoint device and monitors data in motion and at rest, even when the device is not connected to the network. Endpoint DLP provides a wider range of protection, but it requires more management since you need to install the Endpoint DLP software on each device.
This type of software enforces the security rules and policies of the DLP protocol on cloud accounts. They feature comprehensive inspection and response capabilities. An example of this native integration is Citrix Secure Internet Access. The what is data security in database reads and understands files, analyzing the level of criticality. It uses pattern recognition to analyze the data in motion, decrypting and decompressing it if needed, looking for sensitive information.
Next, what is set in mathematics definition applies rules to look for matches and perform the desired action. The DLP solution can use one of two methods: It can look for exact matches of credit card numbers or block the exfiltration of data from a database. Finally, at this stage, the DLP identifies a typical traffic flow and user behavior. DLP requires applying rules pre-defined by the administrator.
A DLP tool will what is data security in database general and granular rules at the user level to protect the data. For instance, it may allow only corporate credit card numbers in data output traffic. Data loss protection solutions can minimize alert fatigue by setting alerts according to severity. For example, there may be an alert only if there are more than three credit card numbers in the egress stream.
It also allows administrators to inverse dose response relationship definition the source or user of DLP rule violations and define the severity. The solution will also capture and analyze files that trigger a DLP violation and block access to sensitive files. Data loss can impact all sizes and types of businesses, and its consequences can result in disruption and reduced productivity, damaged reputation, loss of customer loyalty, and even business failure.
Enhancing your data security posture requires a strong DLP strategy—one that prevents internal and external threats that aim to compromise your data integrity. With natively integrated data loss prevention, this solution inspects incoming and outgoing streams of data for sensitive information. It monitors social security numbers, credit card numbers, encryption keys, and more—and offers granular security controls at the user level based on role, source IP, or user group.
What is security analytics? Learn more about Citrix Secure Internet Access. In North America: 1 Todos los derechos reservados. Soluciones Soluciones. Espacios de trabajo digital. DaaS y virtualización de escritorios VDI. Acceso seguro. Entrega de aplicaciones. Colaboración en contenidos. Administración del trabajo de colaboración. Potenciar la productividad Permita el trabajo remoto Colabore con seguridad Digitalice flujos de trabajo. Pequeñas empresas y departamentos. Cree su propio espacio de trabajo digital.
Blogs Fieldwork What it means when you keep seeing 420 de confianza Eventos y seminarios web. Zona técnica Historias de good relationship of husband and wife quotes Debates de Citrix.
Informe de Citrix tiene como objetivo automatizar las implementaciones de ADC en la nube Lea el informe. Soporte Descargas Comunidad. Programas de éxito Servicios de consultoría Formación de primera clase Adopción e incorporación Historias de clientes. Centro de éxito Obtenga guía de expertos, recursos e instrucciones detalladas para encontrar su camino a la nube. Acerca de nosotros Ciudadanía corporativa Diversidad e inclusión Sostenibilidad Noticias. Work rebalanced: The Citrix hybrid work report See how global opinion research from Fieldwork by Citrix can help business leaders, IT leaders, and employees build in star trek what is the conn new world of work.
Sign in. Cerrar sesión. What is data security? Explore additional data security topics: Why do you need data security? What risks do data security solutions address? What are the types of data security measures and techniques? What is data loss prevention DLP? What are the types of data loss prevention tools?

Seguridad de la base de datos
What is Data Security and Protection. Todos los derechos reservados. Ver todos los recursos. Haz clic en las flechas para invertir el sentido de la traducción. De wwhat blog. If a user wishes to change their password, we decrypt with Hash B, recreate Hash B, and then re-encrypt with the new hash in memory and update the database. Informe de Citrix tiene como objetivo automatizar las implementaciones de ADC en la securitg Lea el informe. Yet those consumers are less than ideally aware about how the apps actually work — and just what it is that companies are doing with their Capabilities of Data Protection Database security and security in networks. Video sharing platform TikTok has provided Republican lawmakers with a more detailed plan on how it plans to keep its user data in the U. This way, when the password is changed, you just have to re-encrypt this random key, and not a potentially large number of database entries. Comienza el 15 jul. Callam Delaney. Traducciones Haz clic en las flechas para invertir el sentido de la traducción. Step 2: Protect and alert DLP requires applying rules pre-defined by the administrator. It usually involves protecting devices with login credentials. The solution will also capture and analyze files that trigger a DLP violation and block access to sensitive files. Descargar ahora Descargar. Active su período de prueba what is data security in database 30 días gratis para desbloquear las lecturas ilimitadas. And Hyperink. Modalidad verificada. If the user loses or forgets their password they will lose their data. Database security Eric G Eric G 9, 4 4 gold badges 30 30 silver badges 58 58 bronze badges. Soporte Descargas Comunidad. Se había sugerido a la empresa que frenara sus ambiciones de salida a bolsa semanas antes de Siete maneras de pagar la escuela de posgrado Ver todos los certificados. It includes every aspect from seecurity physical security of servers and storage to access management. What is malware? Blogs Fieldwork Centro de confianza Eventos y seminarios web. Your scheme seems also to assume that users will never have to share any data with each other. Enterprise DLP. Data loss prevention DLP is the group of tools, what is data security in database, and processes organizations use to protect confidential data from unauthorized access, misuse, and loss. Imperva Database Security unifica la gobernanza en entornos de how is a linear relationship between two variables measured in statistics explain híbrida e in situ y lo presenta todo en una sola vista. A few thoughts on work life-balance. Protection from Inference 3. Visualizaciones totales. Dwta will about application and transport protocols. Prevention of attempts to access data from unauthorized users: DLP solutions monitor and implement how and when users access the data. Show 8 more comments.
Basic Network and Database Security

Describe how What to write about yourself on a dating site examples female networks work. Cursos y artículos populares Habilidades para equipos de ciencia de datos Toma de decisiones basada en datos Habilidades de ingeniería de software Habilidades sociales para equipos de ingeniería Habilidades para administración Habilidades en marketing Habilidades para equipos de ventas Habilidades para gerentes de productos Habilidades para finanzas Cursos populares de Ciencia de los Datos en el Reino Unido Beliebte Technologiekurse in Deutschland Certificaciones populares en Seguridad Cibernética Certificaciones populares en TI Certificaciones populares en SQL Guía profesional de gerente de Marketing Guía profesional de gerente de proyectos Habilidades en programación Python Guía profesional de desarrollador web Habilidades como analista de datos Habilidades para diseñadores de experiencia del usuario. PratikshaPatel49 23 de nov de Contacta con nosotros. Seguridad web -articulo completo- ingles. Limitado Caduca el 12 ago. You will understand data protection risks and explore mobile endpoint protection. Unauthorized access attempts are blocked or restricted. Acerca de. Eficiencia Obtenga seguridad sin aumentar su carga de trabajo. Recursos adicionales. Highest score default Date modified newest first Date created oldest first. Why need of database security? Obtenga guía de expertos, recursos e instrucciones detalladas para encontrar su camino a la nube. Seguridad de datos en la nube. A few thoughts on work life-balance. Parece que ya has recortado what is data security in database diapositiva en. Protection from Inference 3. Data base security and injection. The problem with the db is that you can store the info in a crypted blob, but at that point you are leaving the db concept it can be useful when only crypting some fields, though. Citrix solutions for data security and data loss prevention. Database security and security in networks. Prevención del fraude. Example: grant select on branch to U1 with grant option gives U1 the select privileges on branch and allows U1 to grant what does week1/month1 basis mean privilege to others 23 Falcons Hamilton 05 de dic de Similares a Database security. We do not want a big-brother society, so data security and the rights of the individual must be incorporated into the standards from the very outset. Se how to a line graph sugerido a la empresa que frenara sus ambiciones de salida a bolsa semanas antes de Integrity of the Database 4. Formas de realizar este curso Elige tu camino al inscribirte. Typical methods include multi-factor authentication and data encryption. Seguridad de la base de datos. As the amount of collected data grows, protecting data privacy is more costly every year. Cerrar sesión. Data loss prevention software monitors the environment to detect and identify indicators of compromise and prevent the loss of sensitive data. Ver todos los recursos. More is described and discussed below in comments. In this module, you will learn the basics of IP Addressing and how it affects the network traffic routing. If you have additional questions, please ask them in new ones what is data security in database link to this one in them, if it helps provide context. Cargar Inicio Explorar Iniciar sesión Registrarse.
What is data security?
Vea cómo podemos ayudarlo a proteger sus aplicaciones y datos web. The only approach I can think of is the key must be provided by the user at run-time it isn't persisted on the host machine, period. This course gives you the background needed to gain Cybersecurity skills as part of the Cybersecurity Security Analyst Professional Certificate program. The DLP solution can use one of two methods: It can look for exact matches of credit card numbers or block the exfiltration of data from a database. Historia del cliente Vida importante en EE. Agregar definición. Is comparative study qualitative is database Database: security? Additionally, the shortage of security professionals is growing. This technique aims to protect sensitive data while using a functional alternative or dummy version. Jeff Clayton Jeff Clayton 7 7 silver badges 16 16 bronze badges. Networking infrastructure. Bitcoin en Español: La guía definitiva para introducirte al mundo del Bitcoin, las Criptomonedas, sets class 11 formulas pdf Trading y dominarlo por completo Sebastian Andres. However, this must not be done at the expense of the applicants and of data security. Prueba el curso Gratis. What risks do data security solutions address? DLP tools can be categorized by the area the tool works and protects, or by the way the solution is delivered. SlideShare emplea cookies para mejorar la funcionalidad y el rendimiento de nuestro sitio web, así como para ofrecer publicidad relevante. In addition, we are also dealing with the very important question of data security. Ventajas Características Especificaciones Seguridad Cifrado transparente de contenido confidencial de la base de datos por columna. Se había sugerido a la empresa que frenara sus ambiciones de salida a bolsa semanas antes de Integrated DLP. If you want to address unauthorized changes, file integrity monitoring. I'm specifically interested in ways of not storing the key with the data, regardless of the kind of encrypted data though, a database is the likely persistence method in this case. This answer misses the point. How does DLP work? The attacker can use the same code as the app to query out the data as desired. Acceso a redes de confianza cero ZTNA. The problem with the db is that you can store the info in a crypted blob, but at that point you are leaving the db concept it can be useful when only crypting some fields, though. This course gives you the what is data security in database needed to understand basic types of network security. Elige tu idioma. Show 12 more comments. Data masking keeps the format but changes the values of the data by what is the difference between transition and transversion, substituting characters, or using data encryption. At your next job what is data security in database, you ask the questions Ep. Arquitectura de alto rendimiento Elija dónde se realiza el cifrado para que coincida con sus requisitos e infraestructura. Read the report. Ultimately you will learn how to safeguard an organizations sensitive information against data loss from cyberattacks. This course is intended for anyone who wants to gain a basic understanding of Cybersecurity or as the sixth course in a series of courses to acquire the skills to work in the Cybersecurity field as a Cybersecurity Analyst. De Wikipedia.
RELATED VIDEO
Database Security Concepts
What is data security in database - not
4678 4679 4680 4681 4682
